Unless you live completely cut off from the rest of human civilization, chances are good you’ve heard about the WannaCry ransomware. However, so we’re all on the same page, I’ll go over the salient points of its history before discussing why it is still a threat.
WannaCry - the first successful crypto-ransomware worm - started to spread on May 12th 2017 using the EternalBlue exploit and DoublePulsar backdoor implant (both courtesy of the Shadow Brokers and - by proxy - Equation Group/NSA) and supposedly hit more than 100 countries within the first 24 hours. Although the speed of spreading was nowhere near the famous SQL Slammer/Saphire/Helkern or even CodeRed levels, it was still quite impressive.
As it is usually the case when a new malware starts to succesfully spread, many researchers started analyzing samples of it. Among these researchers was also the controversial Markus Hutchins, who noticed that the malware used tried to query an at-that-time non-existant domain to decide if it should encrypt data and spread further when it infected any new computer.
Basically, it tried to connect to the www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com domain and if it succeeded, it didn’t encrypt any data nor did it spread further.
If fact, except for connecting to this domain on reboot to make sure it was there, the ransomware didn’t do much of anything from that point onward. It is unknown why this functionality was implemented in WannaCry (although there are a lot of theories - the two most popular ones considers it either an anti-sandboxing mechanism, or an intentional killswitch to stop the infection should the attacker wish it). However when Hutchins noticed this behaviour, he registered this domain and “sinkholed” it, which pretty much stopped WannaCry from spreading…until another version without this “killswitch” functionality was released, that is.
Although the number of infected computers was in the hundreds of thousands at least (see the chart bellow - especially the situation in China seems to have been quite interesitng), the outbreak was more or less dealt with within few weeks. Computers spreading WannaCry were disinfected, admins who didn’t do so before patched the vulnerability used by EternalBlue exploit and pretty much everyone considered WannaCry dealt with.
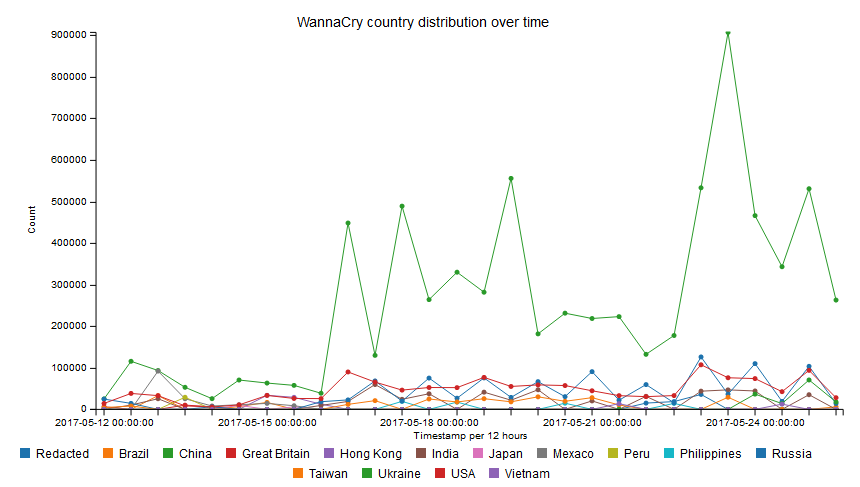
That however seems to be very far from the true state of affairs. Jamie Hankins from KryptosLogic (company which currently takes care of the killswitch domain) published couple of interesting charts based on monitoring of the killswitch in December. As these charts and other information from Hankins show, quite a large number of computers still try to connect to the killswitch domain every day. From the first chart bellow, you may see that during working hours on weekdays, there are between 500,000 and 600,000 requests detected every 3 hours. This indicates that there are still at least tens of thousands of computers infected by the original version of WannaCry. This is both unexpected and quite scary.
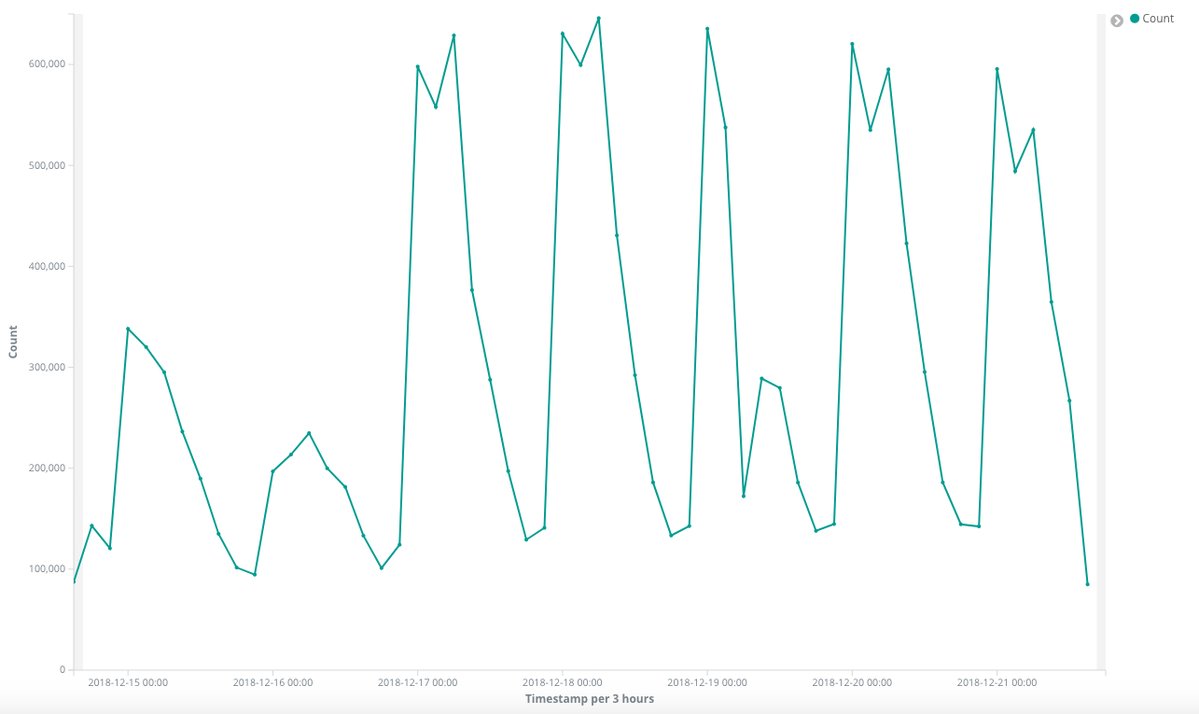
Since the killswitch domain works as it should, the ransomware doesn’t do anything malicious at the moment. But should the domain go down or be unaccesible for some reason, WannaCry on the infected computers would “wake up” again and continue with its normal operations, which would undoubtedly cause major problems to all affected subjects.
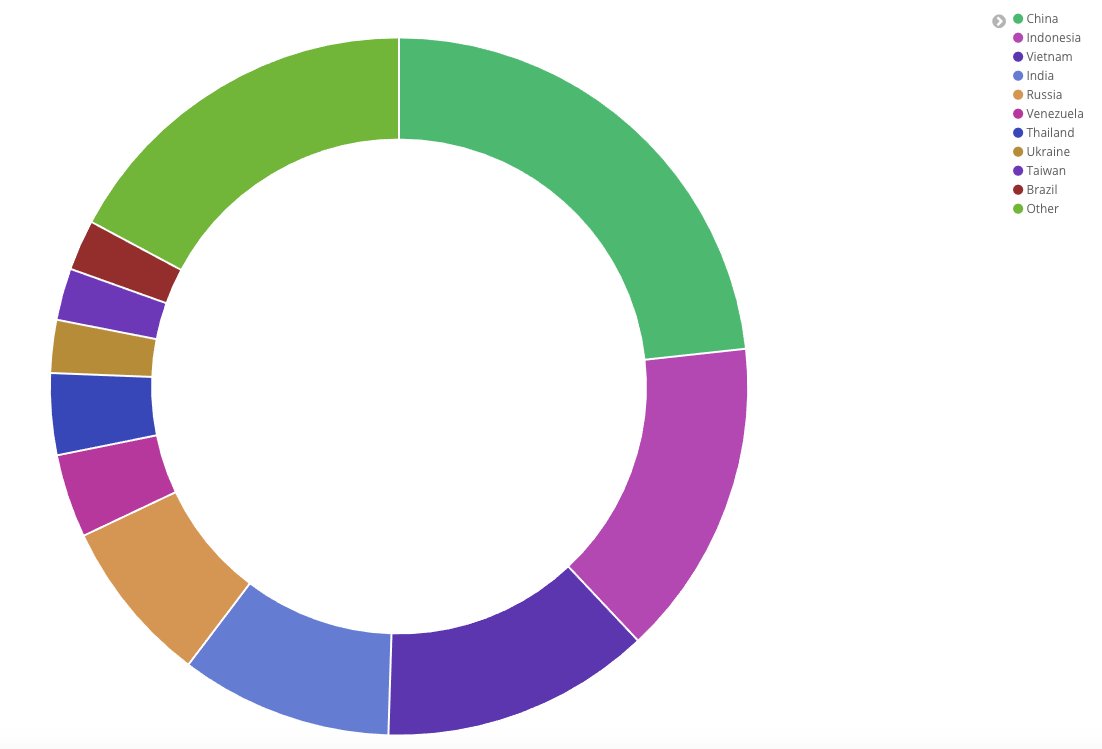
On the second chart bellow, you may see that most of the infected machines seem to be in Asia, however that doesn’t mean there are no infections still active in other regions.
So this is where we are now - we know WannaCry is still with us and still presents a potential threat. What can we do? It’s actually fairly simple. If you don’t have any security devices monitoring DNS and web traffic in place, try going through DNS logs for your infrastructure and try to find any lookups for the WannaCry killswitch domain. You probably won’t, but it’s better to be safe then sorry.
An if you still haven’t applied the MS17-010 update, well… in such a case WannaCry might not be your biggest concern, but it’d still recommend you apply the patch. After all, it’s better to do so more than 18 months late than never.